Deception as a Pervasive and Elemental Force
Chris Flaherty
Introduction
The purpose of this short review is to present a different concept of deception, from how it is typically formulated in classical military doctrine as a tactical component, rather it should be viewed as a pervasive and elemental force in operations. The key argument will be that the world around us, is universally deceptive, and it is the successful ability of commanders in operations to who can bend this environment to advantage, one in which deception has synergistic effects. This approach is based on much earlier military writing, that pre-date the 20th century military doctrinal approach that identifies deception as part of a hierarchy of components, found in various operational concepts. Current doctrine formulations are not necessarily incorrect, as these represent a traditional 20th century approach that sought to harness the forces that shape operations converting these into guiding principles that didactically direct thinking, and planning. However, the doctrine components approach also represents a fundamental problem, ignoring that deception in military art has always had a fundamentally dualistic-role, it is about what impression is created in the opposing commanders’ mind; but it is also about the how the operational picture is distorted by the ‘fog of war’.
The final part of this paper, will present three short commentaries exploring the broader implications of a universally deceptive environment in areas such as: the chaotic urban battlespace, technology convergence and infrastructure insurgency, and the constitutionality question.
Universally Deceptive Environment
The concept of a universally deceptive environment where an opponent is seduced into deceiving him, or herself about the surrounding state of both his, or her own, as well as that of his, or her enemy’s intentions, strengths and capacity is a key component of the first chapter of Sun Tzu’s The Art of War on ‘laying plans’, stating in stanza 18, “all warfare is based on deception” (Giles, 1910). Stanza 18 is often cited out of context of the rest of the commentaries in the chapter – all of which talk of the cumulative effect of many ‘deceptions’ leading to destabilising an opponent’s capacity to successfully prosecute a war. Taking a more modern interpretation, the concept of a universally deceptive environment is part of a wider exploring of the fundamental forces that make up the operational environment. This approach is based on a much earlier tradition in military theory writing, where concepts such as ‘fortuna’ (Machiavelli, 1988); ‘friction and drag’, and ‘fog of war’ (Clausewitz, 1989); or, ‘geographical geometry’ (Jomini, 1862); all sought to identify the fundamental forces that impact on military action. Even in more modern times, psychological features such as ‘isolation and crowding’ were highlighted in the ‘face of battle analysis’ (Keegan, 1976). Identifying how soldiers packed into dense formations limited their access to information. Looking at the backs of forward ranks’ heads and receiving confusing auditory information created misinterpretations. Hearing gunfire and fighting, but not being able to make sense of this led to panic or flight.
As a final note, the fundamental forces approach has never disappeared from contemporary military historical research, and has often been the basis of warfighting analysis, focused of experiential frames of reference – in short, looking at military events in terms of how these are experienced by those who are involved.
Traditional Military Doctrinal Approach
The traditional military doctrinal approach represents a complete objectification, reducing the forces that shape operations converting these into didactic guiding principles (Keegan, 1976). The traditional didactic perspective embedded in classical military doctrine identifies deception as a component. To take the first of two examples, deception is a component of achieving surprise, along with factors such as, ‘secrecy, concealment, originality, audacity and rapidity’ (Ministry of Defence). A not dissimilar formulation is seen in U.S. Joint Doctrine for information operations, which defines deception as,
“those measures designed to mislead the enemy by manipulation, distortion, or falsification of evidence to induce him to react in manner prejudicial to his interests” (Joint Chiefs of Staff, 1998).
Likewise, deception has been identified as a core aspect of influence operations:
“influence the mind and behaviour of the adversary in ways beneficial to the perpetrator” (Hutchinson, 2006).
None of these definitions are not incorrect, however these do not reveal that a much wider effect of deception is possible; and this will be explored next.
Difference Between Traditional Principles and Fundamental Forces Approach
FIGURE 1 illustrates the difference between the traditional principles and fundamental forces approach to deception. The figure on one side shows deception as one of the traditional key elements of a surprise attack. However, deception viewed as a pervasive and elemental force in operations represents a much wider scale of effect. Even though there are some shared variables, deception viewed as a pervasive and elemental force has a clear difference.
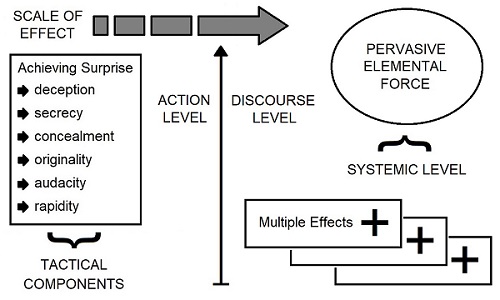
Figure 1: The Scale of Effect of Deception from Tactical Component to Pervasive and Elemental Force
Deception as a component of surprise at its most basic level represents a tactical action. However, due to the inherent nature of deception as an elemental force – beyond the level of tactical action, it also operates on a far more advanced level with potentially disruptive effects on all aspects of the operational environment. This view of deception represents a potential ‘plus-up’ effect, that can generate more ‘potentials’ at the systemic level.
Deception as a Pervasive and Elemental Force
Identifying how deception operates as a pervasive and elemental force can viewed at two levels, namely its discourse and action levels (Flaherty, 2008). In a generic sense, the discourse and action levels are not mutually exclusive; these merge into and deviate from each other, as the strategic, operational and tactical domains focus on the action level, as opposed to its political dimensions – the realm of discourse - and then returns.
At the Discourse Level
Giving out misleading information publicly through internet sites, or videos sent to journalists produces information deception (Kopp, 2005). Tactically, the perpetrator’s aim is to affect intelligence and security analysis, and thus public perception of what are potential targets, and how these would be attacked. This effectively diverts attention from more likely targets. This helps conceal operational activities, as well as exhausted the resources of authorities, which may have been diverted to protect a target, which may not be a target at all. An example, would be where public debate among news and political commentators appears influenced by misleading and deliberately ambiguous terrorist messages. Another example, was the assessment from the 2005 London Underground attacks, that noted the miss-interpretation of the original UK government intelligence assessments in that year. The predominant thinking at the time was argued to be faulted, as attacks were assumed to occur on the UK rail system and against “iconic targets” (Intelligence and Security Committee Report, 2006). While the Committee found that the UK Transport Security Team regarded the likelihood of an attack as high, it was also likely that intelligence assumptions may have ultimately misdirected security resources away from normal commuter routes, leaving these open to attack.
At the Action Level
Tactically speaking, nearly all operations employ one of more classical deception techniques (Haswell, 1985). Equally, nearly all tactics are supported by acts of deception. For instance, placement of a vehicle concealing a lED on a street where it will not be noticed, because it is a type normally parked there, at that time; or a person carrying a backpack, where people are always carrying one; constitutes the use of classical deception techniques.
Exploring this concept further, take for example, the situation where once an attack has occurred the polemics generated by commentators shifts the focus onto ‘what was attacked’, as an indicator as to what was (or is) the perpetrator’s message. In classical thinking, the relationship between military action and political discourse is a transactional one (Clausewitz, 1989). Problematically, this is not always the case. For instance, in the case of an opportunistic attack against a random target, presenting itself without warning or reason. Such an action represents a type of information deception. That is, the ambiguity of the action has the given potential to cause confusion and misdirection that can have universal impact on all the parties to a conflict even if they are not the intended audience.
Broader Implications of a Universally Deceptive Environment
As stated the final part of this paper, will present three short commentaries exploring the broader implications of a universally deceptive environment in the areas of: 1) The chaotic urban battlespace; 2) Technology convergence and infrastructure insurgency; and, 3) The constitutionality question. These overviews are intended as exploratory analysis, serving to illustrat some of the likely flow-on of universal deception, in upcoming and future operational scenarios, that are intended for later development.
The Chaotic Urban Battlespace
Representing a conceptual shift from the ‘irrational tenth’ (Lawrence, 1920), the chaotic battlespace is typified by unplanned manoeuvre, and happenstance encounter. Central to this, is the capacity to deal with a deceptive environment. Viewing deception as a pervasive and elemental force helps in our understanding of the chaotic urban battlespace. Recognition of the complex environment as having built-in or an inherent level of information deception, opens our understanding of the potential ‘plus-up’ effects. For instance, a deceptive event can generate more ‘potentials’ at the systemic level of operations, which an attacker or defender can both exploit, to greater or lessor success.
The key dynamic shift in the battlespace of the previous decades, is driven by a plethora of environmental, economic and technological factors, to name a few:
- By the mid-21st century, the bulk of the world’s population will live in sprawling cities along coastal regions. Future operations will be conducted in these increasingly dense, and masively over-populated mass urban agglomerations.
- The key symptom of operating in a densely packed urban place is that the combat environment overlays the civil; namely, military and security operational concepts will need to rapidly adapt to dynamic and sudden shifts between high intensity operations, to assisting civilian populations basic survival needs, and ensuring minimum disruption to the ongoing operation of economic, human, power, information etc systems that network throughout the rest of the mass urban agglomeration.
A key effect of operating in the mass urban agglomeration challenges conventional thinking that opposing commanders will seek combat supremacy, by imposing deception and artificial realties into the opposing force’s OODA loops. However, these very operations are themselves immersed in the 24/7 info sphere generated by the mass urban agglomeration. Constant coverage from blogging and phones, where news, fake-news and conflicting facts risk drowning-out a coherent operational picture. Creating in the end the ‘new irrational sphere’.
The new irrational sphere will place enormous stress on the operational and technological supports to full-situational awareness and full-sensor-shot; that will constantly need to overcome the inherent deception within any crowded environment. This later factor alone will drive much of the capability needs for the coming decades.
A central feature in exploiting deception as a pervasive and elemental force is the detachment of forces from traditional command and control, with a greater emphasis on events directed by command and influence. This trend will culminate in opponents seeking full advantage from marauder, or swarming tactics. A traditionally wild card in combat operations, marauders operate independently and self-sufficiently aggressively hunting down targets, sometime swarming towards, other times moving erratically over terrain. The erratic aspects of marauder-movement give several advantages over conventional forces, namely: unpredictability of their next move; lack of any command function to attack; lack of foreseeable motive – beyond the obvious need to hunt and destroy.
Finally, as a basic rule - marauder speed and aggression have a greater opportunity to overwhelm conventional forces, where these are directed by force moderation doctrine. The reason for this, is that crazy tactics and operations (which are largely the basis of the marauder’s operational art) have a fundamental informational advantage of hiding from view the force-in-being, behind a screen of crazy attacks and actions, till it can move silently into position virtually on top of its intended target; striking with full force and terrific violence.
Facing these new crazy-opponents, new doctrine on deception, understanding its pervasive and elemental nature will be needed, to better understand the erratic nature of modern combat, as well as drive capability development.
Technology Convergence and Infrastructure Insurgency
It is premised that without the trickery aspects for successful information deception, the adversary could effectively have, “battlefield transparency” (Wang, Li, 1995). The basis of this argument, is that –
“‘battlefield fog’ used to be a major problem troubling battlefield commanders … with digitized units, the battlefield is transparent” (Wang, Li, 1995).
The transformation argument as it was later framed, runs a similar logic, namely -
“the transparency afforded us by the information age creates predictability, optimization and efficiency” Cebrowski (2004).
Illustrating how deception is a pervasive and elemental force in operations, it can be argued that commanders (and their forces) will struggle to maintain information dominance, in the face of a complex environment that is easily to misread. This elemental factor, viewed from technology convergence, will play a significant role in the ongoing development of deception, as new emerging technologies are adopted. For instance, the adoption of augmented reality glasses, could become a significant factor in deception and counter-deception, affecting the wearer’s mental outlook and motivation. It could well be the case, as predicted in science fiction, that future warriors will look at the world through augmented reality as a means to reinforce ideological and religious universal views; which then opens the potential that the underlying systems are hacked with the intention of disorienting the wearers.
In the realm of infrastructure insurgency, we are seeing insurgency just not institutional replacement but also technology replacement. This is where the ‘good-guys’ and ‘bad-guys’ are using the same twitter/social media, CCTV, etc technology. The new battlefront will be the speed at which either side, or multiple sides can connected-to, co-opted, and hack local CCTV to give themselves wider area surveillance, and situational awareness. Connected to new generation mobile micro-weapons platforms, such tactics, techniques, procedures and technologies will add to the already confused battlespace. These trends are already foreseeable, in 2016 it was reported that the Gulf Cartel used heavy machinery to remove a U.S. Police camera network near the Texas-border (Cartel Chronicles, 2016). This was done to effectively blackout the border region and deceive local U.S. authorities as to the extent of cartel operations. In 2016, it was claimed that Hezbollah hacked numerous security cameras in Israel replacing images with the intent to destabilise Israeli security operations (TOI Staff, 2016).
The potential co-opting/reconfiguring of CCTV systems could be used to mount a deception, and points to a far more complex problem namely the trend towards sharing of the logistic base by friend and foe alike; leading to a situation where combatants becoming embedded within the same local power, and information infrastructure (Flaherty, 2015). In short, both friend and foe alike actually share the same logistics infrastructure, a direct consequence of the regional and global connectivity of information and power systems. Conceptually, this merging of the friend-and-foe’s logistic base, into one-and-the-same has fundamental implications for the use of deception operations as these are primarily operated via the communications infrastructure, which if shared by both combatants simultaneously, both sides will be subjected to the same potential threats; namely, each side will be able to find ways to co-opt, distort and redirect the others deception operation for their own purposes. As an added level of complexity, this scenario does not exclude the possible third, and forth parties, such as international hacker-activist, criminal, or terrorist groups entering the fray for their own purposes.
The Constitutionality Question
As a final exploratory comment, given the fundamental and pervasive nature of deception, there needs to be recognition that there are national security and constitutionality issues that impinge on governments conducting a deception campaign. The constitutional question - how to choose, apply, mix or balance the individual elements of defence power as an expression of national power, involves the constitutional laws issues - of what can a country do (or cannot do) given its constitutional basis? (Edwards, Walker, 1988; Flaherty, 2003) This is a complex question about how does a country’s military actions directly reflect it politics, its government etc. As discussed previously, at the discourse level of conflict, this identifies where adversaries battle to interpret and give meaning to their actions, and those of their opponents. Locked in polemics each side seeks to win over the political dimension. Viewed as an opportunity for deception, the politics of conflict could be fundamentally distorted, where deceptive information is manipulated, manufactured and broadcast to re-frame the conflict, distort its justification, and its meaning. A national government vigorously running deception to reinforce operations face a fundamental conundrum, if false and misleading statements quickly feed into the 24/7 info sphere adding a political dimension that may take on a life of its own, destabilizing government efforts, and the very operations they are trying to support and sustain, and public confidence – asking what is going on?
References
Cartel Chronicles. 2016 Free Rein: Gulf Cartel Used Heavy Machinery to Remove Police Camera Network near Border. Breitbart.com (11 April). http://www.breitbart.com/texas/2016/04/11/hold-mexicos-gulf-cartel-takes-police-camera-network-near-texas-border/
Cebrowski, A.K. 2004 Statement on Terrorism, Unconventional Threats and Capabilities. Director of Force Transformation. Office of the Secretary of Defense. Statement before the Subcommittee Armed Services Committee, United States, House of Representatives (February 26).
Clausewitz, C (Von). [Paret, P. Howard, M.E. Translators] 1989 On War, Indexed Edition Reprint Edition. Princeton University Press (Reprint Edition).
Edwards, G.C. Walker, W.E. 1988 National Security and the U.S. Constitution: The Impact of the Political System. Baltimore: Johns Hopkins University Press.
Flaherty, C. (2015) The Role of CCTV in Terrorist TTPs: Camera System Avoidance and Targeting. Small Wars Journal online. http://smallwarsjournal.com/jrnl/art/the-role-of-cctv-in-terrorist-ttps-camera-system-avoidance-and-targeting
Flaherty, C. 2008 3D Tactics and Information Deception. Journal of Information Warfare (7:2).
Flaherty, C.J. 2003 Australian National Security Thinking, Defence Force Journal (160).
Giles, L. 1910 The Art of War Sun Tzu. British Museum.
Haswell, J. 1985 The Tangled Web: The Art of Tactical and Strategic Deception. John Goodchild, Wendover.
Hutchinson, W. 2006 Information Warfare and Deception. Informing Science.
Intelligence and Security Committee. 2006 Report into the London Terrorist Attacks on 7 July 2005, Houses of Parliament, UK (May).
Joint Chiefs of Staff [U.S. Government]. 1998 U.S. Joint Publication 3-13. Joint Doctrine for Information Operations. Washington (October).
Jomini, A-H (Baron de). [Mendell, G.H. Craighill, W.P. Translators] 1862 The Art of War. New York: G.P. Putnam.
Keegan, J. The Face of Battle (London: Jonathan Cape, 1976).
Lawrence, T.E. 1920 The Evolution of a Revolt. Army Quarterly and Defence Journal (October).
Machiavelli, N. [Skinner, Q. Price, R. Editors] 1988 The Prince. Cambridge: Cambridge University Press.
Ministry of Defence [UK Government]. British Defence Doctrine. Joint Warfare Publication 0-01 (Second Edition).
TOI [Times of Israel] Staff. 2016 Hezbollah: We hacked into Israeli security cameras. The Times of Israel (20 February 2016). https://www.timesofisrael.com/hezbollah-we-hacked-into-israeli-security-cameras/
Wang, B. and Li, F. 1995 Information Warfare, Academy of Military Science, Beijing. Paper excerpted from articles in Liberation Army Daily, June 13 and June 20.
