Adding the Warrant to Your Quiver: Ten Tenets of Warrant Based Targeting
Jeffrey Barta, Jessica Caddell, and Scott Goldman
The American military has witnessed many changes during the past decade of overseas contingency operations (OCO). These have forced adaptations in the tactics, techniques, and procedures (TTPs) of our ground forces. Among these adjustments is the inclusion of host nation (HN) laws into the repertoire of methods available for establishing and enforcing a stable security environment. Known as Rule of Law or colloquially as RoL, this system seeks to enable the fledgling legal systems of host nation governments with internationally recognized principles in addition to the laws of armed conflict (LOAC) employed by foreign security forces. The use of warrant based targeting (WBT) is an effective process within the RoL that provides security forces with a different arrow in the quiver to defeat threats to the security environment. Similar to the other adaptations that our military has made, adding warrants to the quiver of arrows available to tactical units’ targeting methodology requires knowledge, training, and flexibility. This article provides ten tips focused at the tactical level and derived from combat operations in Afghanistan to assist combat leaders on advising host nation security forces to use warrant based targeting in the RoL. The following are ten tenets offered to tactical level leaders and Security Force Assistance Advisors:
- Understand the HN Rule of Law
- Reflect the HN system
- Shift institutional energy from finishing to finding
- Create WBT work teams
- Strive for HN sustainability
- Create synergy between HN systems
- Overlay the overlay
- Classify information at the lowest level
- Hone a specialized strike force
- Advise the advisor
1. Understand the HN Rule of Law.
Successful WBT uses HN law as a tactical tool to remove insurgents from the battlefield. To do so requires understanding the HN criminal justice system. The Afghan Constitution and the Interim Criminal Code for Courts (ICCC)[i] lay out the Afghan criminal justice process. To the American perspective, this process follows a familiar method of (A) gathering evidence, (B) obtaining warrants, (C) actioning suspects, (D) interrogating and investigating detainees and physical evidence, (E) submitting the case for prosecution, and (F) prosecuting the case through appeal. At each stage in Afghanistan, WBT success requires advisors to engage and support different players in the Afghan criminal justice process.
- Gathering Evidence. All Afghan National Security Forces (ANSF) pillars in Afghanistan may be involved with gathering evidence against insurgent-criminals. Most frequently, RoL advisors will work with investigators from the National Directorate of Security (NDS), Afghan Uniformed Police Counterterrorism Department (AUP CT), or Afghan Uniformed Police Criminal Investigation Division (AUP CID). There is no timeline on how long these investigators might spend gathering evidence and preparing files against specific enemy targets. Realistically, ANSF, like investigators in the West, are investigating an array of individuals and networks simultaneously.
- Obtaining Warrants. Once the ANSF has enough evidence to arrest an insurgent suspect, the ANSF must request permission from a Saranwal – a hybrid prosecutor and investigator – to make the arrest. [ii] The Saranwal will determine whether sufficient evidence exists to grant an arrest warrant to issue to ANSF. However, if ANSF witness a crime unfold or enter a situation where it is impossible to contact a Saranwal before evidence is destroyed or a criminal flees, they may make a warrantless arrest in what ANSF frequently call the “emergency exception.” In reality, the exception sometimes swallows the rule. Still, in the Afghan province on which this essay is based, the Saranwal issued warrants to both ANSF and Coalition Forces (CF). Figure 1 below shows a copy of an arrest warrant, based on biometric evidence linking the suspect to an IED strike, granted by the Saranwal to CF. Key to supporting WBT at the warrant phase of the process is for CF to establish a strong relationship with the Chief National Security Saranwal of the Province. This Saranwal can review CF evidence; provide visibility and track priority prosecutions; grant warrants to CF on biometric-based targets; and, in a more sustainable fashion, work with ANSF pillars to turn CF-based evidence into warrant requests from ANSF investigators.

Figure 1: An example Afghan arrest warrant issued to ANSF and Coalition Forces.
- Actioning Suspects. With a Saranwal-granted warrant in hand, ANSF can then action the targets and make arrests. In the Afghan province that serves as the basis of this essay, this was the hardest step for CF to influence. It was easy to obtain warrants and support ANSF warrant requests, and it was easy to supplement Afghan prosecutions once an arrest was actually made. However for myriad reasons, it was difficult to encourage ANSF to arrest targets on whom a Saranwal had already issued a warrant. [iii] WBT advisors – whether RoL attorneys, SFAAT intelligence advisors, or maneuver-element partners to ANSF – must be patient and persistent with all their counterparts in encouraging the united effort and direct action discussed throughout this essay.
- Interrogating and Investigating Detainees and Physical Evidence. When ANSF initially capture a detainee, they are required to alert the Saranwal within 24 hours of the arrest and seek further guidance or ratification of the arrest if they made it without a warrant.[iv] The Saranwal then has 48 hours to interrogate the detainee and examine physical evidence.[v] The Saranwal must decide whether to accept the case and authorize 15-days of detention (from the moment of arrest) during which he and the arresting ANSF authority may continue to investigate the case.[vi] The Saranwal can obtain another 15-day extension from the court, granted routinely, before he must send the case to the primary court (indict).[vii] During the interrogation and investigation phase, advisors will have to maintain close contact with the investigating agency: NDS or possibly AUP CT for insurgent-related crimes and the AUP for general crimes. A RoL advisor should also maintain contact with the Saranwal and ensure timelines are met and provide sufficient evidence to ensure continued detention and a thorough investigation. Supporting such investigations through mentorship or intelligence sharing, CF advisors can sometimes make the difference between priority targets being released for and being forwarded to prosecution.
- Submitting the Case for Primary Court Prosecution. Once the Saranwal has obtained sufficient evidence to prosecute a case – which usually requires witness statements or intelligence reports, physical evidence from the crime scene, and/or a confession – he will submit the case file to the Primary Court. The Primary Court then holds a trial, which is not an adversarial event like we are used to in U.S. Courts. Rather, an Afghan Primary Court Trial is really a trial process, during which the Court has two months to hold hearings, question witnesses, and review documentary and physical evidence.[viii] The trial will culminate with an opportunity for the accused to offer arguments and a defense, but the entire event more resembles a European-style inquisitorial trial than an American adversarial trial.[ix] CF advisors can maintain visibility over the trial process through direct contact with the judges or, even more effectively, hiring Afghan national attorneys to serve as Afghan Legal Advisors who can attend trials and meet with judges for updates. There is little CF can (or should) do to influence trial outcomes once CF has passed all available evidence to the Saranwal to include in his case file. It is important to remind judges when CF has an interest in a case, as the scrutiny itself raises the bar for performance and, in rare cases, raises the price for corruption.
- Prosecuting the Case through Appeal. Once a Primary Court has reached a decision, both the accused and Saranwal can appeal to an Appellate Court, which has an additional two months from the date of the primary decision to reach an appellate decision.[x] Again, a strong relationship between CF and appellate judges can ensure CF interests are represented in court and prevent cases from falling between the cracks. Appellate courts tend to affirm Primary Court decisions or increase the severity of sentences. Following the Appellate Court’s decision, the case is then moved for final review by the Supreme Court of Afghanistan in Kabul, which has five months to reach a decision.[xi] Again, the Supreme Court typically affirms its lower court decisions, though it has de novo review authority and can review and change law, fact, findings, and sentences.
Adding the entire process up, from the day of arrest to a Supreme Court decision, an effective arrest of an insurgent can remove that insurgent from the battlefield for up to ten months and often longer as timelines are exceeded throughout the process. Effective WBT advising requires CF engage law enforcement and judicial actors at every stage through this process to ensure priority cases remain on track with strong evidence.
2. Reflect the HN system.
To synchronize with the Host Nation Rule of Law system, tactical level units should mirror their battle rhythm to be similar to the HN forces within their area of operations. A method to do this is to align the doctrinal targeting process with the WBT process. U.S. doctrine to target high value individuals follows a methodology known as F3EAD or Find, Fix, Finish, Exploit, Assess, and Disseminate.[xii] This system was derived from Special Operations Forces conducting Foreign Internal Defense (FID) in the 1980s in Latin America.[xiii] This system re-emerged into doctrine to assist Brigade and Battalion sized units to fight Counter Insurgency (COIN) campaigns in recent OCO operations. In simplified terms, F3EAD is another version of the Military Decision Making Process (MDMP), which is a way to conduct problem solving. Under different names and methodologies, HN forces conduct problem solving in their own method. Advisor forces should attempt to adjust their planning processes to bring together their effects in the operational environment.
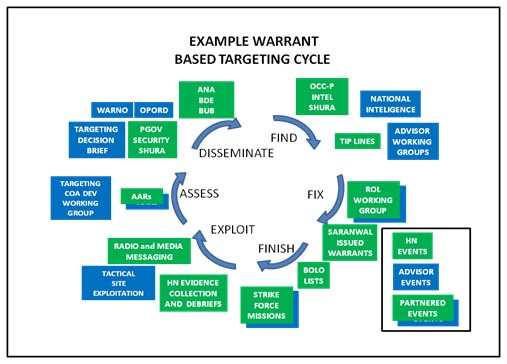
Figure 2: Example warrant based targeting cycle within the F3EAD targeting methodology.
The above diagram depicts the significant events within the F3EAD cycle from a province of Afghanistan. This shows the many events, meetings, and actions nested between the advisor forces and the host nation forces. This cyclical targeting method serves to defeat insurgent networks by focusing the counter insurgent effects on targeted individuals and exploiting success to develop and find additional targets. While the advisor and host nation methods may differ in their planning and targeting process, the constructs of F3EAD can align and synchronize their efforts.
In many provinces in Afghanistan, the local government and security forces operate on a weekly schedule. Slightly offset from Western schedules, the day of rest is on Friday and the week starts in earnest on Saturday. Generally, governmental problems are discussed during weekly Shuras, or meetings, which develop into decisions and plans. Within the security forces, some Western trained Afghan Army leaders combine the MDMP within the weekly cultural rhythm to identify and solve problems on a weekly basis. Advising forces should mirror their battle rhythm to reflect that of their counterparts. This will serve to synchronize the planning timelines of both organizations and create unity of effort between the targeting cycles.
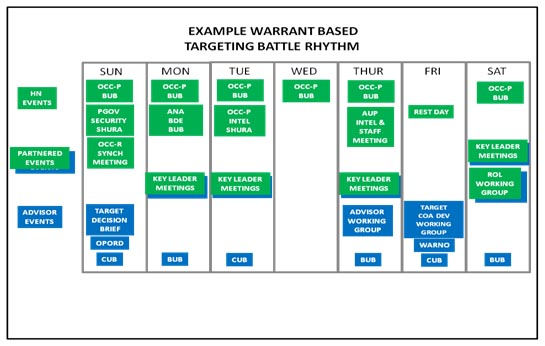
Figure 3: Example warrant based targeting battle rhythm depicting the host nation planning events and the advisor planning events.
The above figure depicts an example targeting cycle where the host nation forces plan in a weekly cycle and the advisor forces reflect that of their counterparts with a one-week cycle. The advisors attend select host nation shuras and conduct key leader meetings during the week in order to implement directed actions from the previous targeting cycle and assess their progress. Planning events during the host nation workweek, Saturday through Thursday, are conducted in a decentralized manner between the advisors and their counterparts within their war fighting functions. Intelligence advisors attend the host nation intelligence events and operations advisors engage their counterparts of the same occupation. The advisors then maximize the slow periods of rest on Thursday afternoons and Fridays to come together into several working groups modified from FM 3-60 as the targeting working groups and targeting board.[xiv] During the advisor working group the advisors assess their counterpart forces and determine the successes and progress of previously implemented plans; many Army units term this meeting an “assessment working group.” On Friday, the advisor forces propose and prepare courses of action (COA) to plan future actions addressing the assessments from the previous day’s assessment working group. The outputs from the COA development working group are prioritized targets and a warning order (WARNO) preparing subordinates for future operations. The proposed COAs for upcoming missions, tasks, and actions are then presented to the commander during the targeting decision brief on Sunday for final decision and prioritization before implementation. In the Afghan province from which this example was derived, the Provincial Governor usually led a major “Security Shura” on Sundays, where the government delivered plans and orders to its security forces. By placing both the host nation and the advisor decision meetings on the same day, plans complemented each other during the upcoming week and freed staff and subordinate units to focus on their war fighting function and counterparts without distraction from centralized meetings. In this manner, overlaying the F3EAD cycle over the host nation planning timeline creates a synchronized battle rhythm maximizing the planning efficiency of both counter-insurgent organizations and increasing their effects on the targeted networks.
3. Shift institutional energy from finishing to finding.
The F3EAD model effectively balances cyclical planning with the cyclical efforts of forces in the field to achieve the commander’s desired end state. According to FM 3-60, “Targeting seeks to achieve effects through lethal and nonlethal actions in a systematic manner. A targeting methodology is a rational and iterative process that methodically analyzes, prioritizes, and assigns assets against targets systematically to achieve those effects that will contribute to achieving the commander’s objectives.”[xv] While preparing to deploy to a theater of operations and implement a WBT process based on RoL, the institutional mindset, training time, and resources must be prioritized differently from traditional lethal based targeting systems. Simplifying the F3EAD model below to focus on the find, fix, and finish aspects of targeting will serve to illustrate this shift.
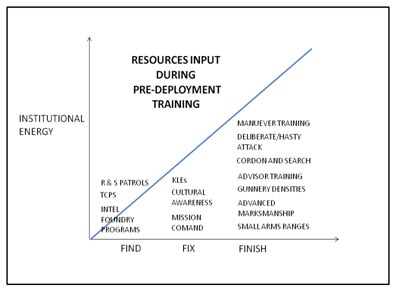
Figure 4: Traditional training focus areas for lethal targeting [xvi].
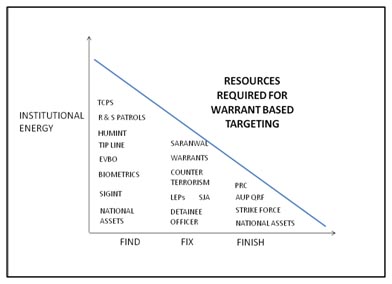
Figure 5: Required resources necessary for warrant based targeting that require a pre-deployment training focus[xvii].
These diagrams compare the institutional energy required in training and during conventional lethal based targeting operations with WBT within the RoL. Conventional methodologies rely heavily on the finish aspects of an operation whereby the military invests many resources to mass the effects of combined arms in order to overwhelm an enemy. Conversely, in using a WBT approach, the organization must devote the majority of its energy to finding and fixing the enemy force.
In a 2012 essay on WBT, Kevin Govern stated: “The successful carrying out of warrant-based targeting requires not only force necessary to subdue or to bring into custody the subject, but also perhaps even more importantly the deliberate efforts of applied, nonviolent law enforcement skills.” [xviii] These skills are required to develop a target through the means described in the seventh tenet: reconnaissance and intelligence. Skills on which to focus the efforts of tactical forces to find targets are Evidence Based Operations (EvBO), including the successful employment of biometric systems and tactical site exploitation (TSE). The unit’s intelligence function must understand the nuances of signal and human intelligence (SIGINT & HUMINT) as well as the many national level assets available to the ground forces serving as advisors. The advisor force must also apply the skills of several agencies such as law enforcement professionals (LEP); the unit’s judge advocates (SJA); and the Saranwal. These agencies are integral to assisting the advisors and the host nation forces to fix the enemy in the non-lethal sense using warrants during operations to detain targets and remove them from the field through the judicial process. These agencies are rarely available in home station pre-deployment training, yet must be understood to enable their rapid integration into the WBT work team as discussed in the fourth tenet. Last, the advisor force must maintain a specialized strike force to partner with specialized host nation forces who are responsible for the tactical actions against the targeted individuals. This is discussed further in the ninth tenet.
While figures four and five show the disproportionate relationships in organizational energy input into the find, fix, and finishing aspects of targeting; significant resources must also be invested into the exploiting, assessment, and dissemination facets of the WBT process. Success within warrant based targeting should be exploited through the host nation judiciary in order to achieve convictions with lasting punishments. Evidence discovered during TSE must be carefully tracked and provided to the prosecutor. Units may further enhance exploitation through photos, sketches, and statements produced by both the U.S. strike force and, more importantly, by the host nation security forces, which add to the case against a targeted insurgent. Assessments during WBT are an ongoing cyclical process to analyze successes and areas for improvement within the host nation RoL. Advisor forces should assess the capabilities, confidence, and outreach of their host nation security partners using measures of effectiveness (MOE) and measures of performance (MOP) of their HN counterparts. The dissemination phase of F3EAD is a facet of WBT that occurs in many parts of the process and offers many areas for advisor forces to apply their efforts. Advisor forces must streamline their own information systems and knowledge management to flatten their organization and create sufficient shared understanding between all staff work teams and subordinate advisor elements. Advisor forces must strive to connect with their HN counterparts to facilitate intelligence sharing, disseminate targetable warrants, and establish priorities between the various agencies of the host nation security forces.
When used for WBT, the F3EAD cycle is a good model to focus the efforts of an advisor force. Targeting presents many areas for which organizational energy must be invested to find, fix, finish, exploit, analyze, and disseminate insurgent targets under the RoL construct. Placing leader emphasis on these areas during pre-deployment training and during cyclical planning will maximize the effectiveness of the advisor force.
4. Create WBT work teams.
Beyond the many non-traditional aspects of training required to implement WBT, the advisor force must also redefine traditional staff roles and create specialized work teams able to focus on the specialized aspects of targeting within the RoL. Most Western and NATO countries including the United States base their staff on the Prussian model recently modified into function cells based on the war fighting functions. As there are several functions applicable to WBT that do not fall within the seven war fighting functions, the advisor force must create specialized work teams that fill capability gaps.
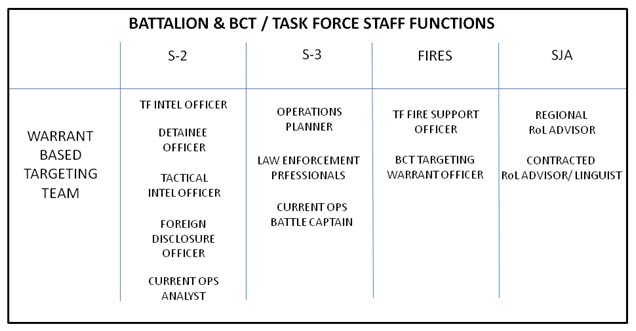
Figure 6: Example of a functional work team to facilitate the host nation warrant based targeting process.
There are many functions required to assist with warrant based targeting that do not fall within normal positions on the Modified Table of Organization and Equipment (MTOE). Conventional forces placed in an advisory role must create several new positions that enable the warrant based targeting process. As listed in the figure above, these positions fall within traditional staff functions, but must work as a unique, functions based team. The detainee officer within the S2 section focuses on all aspects of detainees and tracks them from the point of capture through the host nation penal system. Within the S3 section, the Law Enforcement Professionals (LEP) are contracted former police officers who advise the conventional forces on civil law enforcement and assist the security force advisors with processing, submitting, and tracking biometric and physical evidence for use by the host nation prosecutor. Lastly, and arguably most important is the RoL advisor; a lawyer from the brigade staff judge advocate (SJA) office focused primarily on mentoring members of the host nation judicial system. Along with his or her contracted local advisor, these two members of the SJA section must work in conjunction with the security force advisors to serve as conduit of information flow to the local national prosecutor. They further help in the “fix” and “exploit” aspect of targeting to ensure that the warrants are legally valid and result in convictions with significant judicial sentences to remove the insurgents from the operational environment.
Several conventional staff roles within the task force should be revised to support the warrant based targeting process. Within the S2 section, the TF intelligence officer and the tactical intelligence officer center their efforts on the “find” and “assess” aspects of targeting by monitoring the many forms of intelligence to develop targeted persons of interest. The foreign disclosure officer assists all members of the work team with information sharing between the advisors and the security force. The eighth tenet describes more suggestions on this process. The operational planner and current operations battle captain from the S3 section serve to coordinate and synchronize the assets necessary to conduct R & S and strike force operations. They further must work to connect the various host nation security forces with their strike force from the advisor element for synchronized, partnered operations and are further involved in the “finish” and “disseminate” aspects of F3EAD. The TF fire support officer drives the targeting process to aid the commander in selecting and prioritizing proper targets and publication of the targeting orders and associated products. The BCT targeting warrant officer should be included in the WBT work team in order to synchronize targets with higher echelon priorities. These two team members serve as the primary proponents of the “disseminate” aspect of the targeting process.
Modifying conventional staff roles and uniting them with many newly created positions is necessary for WBT to be effective. The members of this specialized team should work together within the battle rhythm process described in the second tenet under the oversight of the task force executive officer. Combined together, the warrant based targeting work team is a method to administer the F3EAD process for tactical operations by a task force level advisor force.
5. Strive for Host Nation sustainability.
The enduring mission of an advisor force mission is to increase the capacity and confidence of the host nation forces to persist and protect their populace beyond the departure of their advisors. Rule of Law provides the means to deliver lasting security leading to enduring stability as described in the Small Wars Journal: “Today, our strategic success hinges on our ability to transition the responsibility for all governance functions, rule of law responsibilities, economic and security institutions to the HN National, Provincial and Regional establishments.”[xix] Advisor forces who execute WBT should always maintain a focus on transforming the process to be sustainable by the host nation. While conducting an expeditionary mission in a foreign area, the advisor force will possess many resources not available to the fledgling host nation government. These resources, listed in Figure 4, are crucial for conducting WBT but must not be the centerpiece of the task force’s efforts. Instead, the advisors must focus on developing the resources available to the host nation.
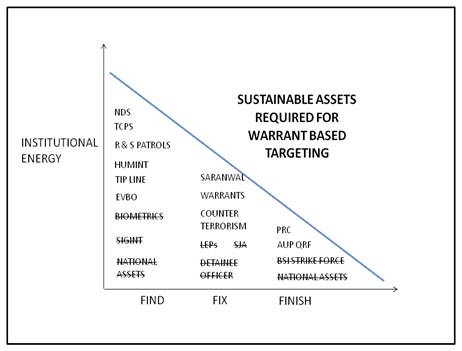
Figure 7: Example of host nation sustainable assets available for WBT from a province in Afghanistan.
Using the example from Afghanistan, the figure above depicts the resources required for WBT and highlights those that are sustainable to the provincial and district security forces and judicial system. The NATO led coalition provides many enablers to WBT, including reach-back access to the national intelligence structure, which will no longer be available upon the completion of the ISAF mission. While conducting WBT, the advisor force must be weary not to rely too heavily on the resources, lined out in Figure 7, and instead be cognizant of those resources available to the host nation. This may mean relying more heavily on human intelligence and sacrificing crucial signals intelligence to “find” and “fix” potential targets or by making sure that the information releasable to the host nation as described in the eighth tenet. It may also mean placing extra training emphasis on the host nation forces to conduct effective reconnaissance and surveillance (R & S) patrols or traffic control points (TCPs) to “find” targets. A simple technique to assist the host nation forces is to create a be-on-the-look-out-list (BOLO) with pictures of all active warrants for distribution to the host nation. Members of the WBT work team should mentor the host nation prosecutor and counter terrorism agents to develop the “fix” and “exploit” phases of the targeting cycle. This is accomplished by connecting the local prosecutor to the national biometric evidence laboratory and to other security force agencies to create lasting synergistic relationships as described in the sixth tenet. Last, extra attention should be placed on the HN strike force to “finish” targets with a raid or cordon and search with warrant in hand. Techniques to develop the strike force are further described in the ninth and tenth tenets.
There may be pitfalls to focusing on sustainability, such as informants unwilling to make statements for fear of retribution or host nation commanders who withhold issued warrants from their subordinates out of security concerns. Advisors should accept the frustrations in exchange for the growth that develops as everyone learns the WBT cycle together. Advisors may be tempted to conduct WBT with their own mature and reliable systems, but they must be prepared for inefficiencies and setbacks in the WBT process as the host nation process develops into a sustainable system supporting the Rule of Law.
6. Create synergy between HN systems.
Another tenet to help make the WBT system sustainable is to create synergistic links between the many arms of the host nation security and judicial systems. In the contemporary operating environment, the host nation may have several agencies from different security ministries fighting against the insurgent forces. These agencies include the Army, local police, national police, the investigative service, and paramilitary security forces. In Afghanistan, ISAF has sought to unite the pillars of the Afghan Security Forces under the RoL framework and states that “EvBO requires cooperation and common understanding along the entire spectrum of actors, from initial response and/or discovery, through investigation, warrant issuance, collection and preservation of evidence, arrest and prosecution by trial, sentencing and incarceration as appropriate.”[xx] This “cooperation and common understanding”[xxi] is necessary for each step of the F3EAD but most critical for finding targets with shared intelligence and disseminating the responsibility to “finish” each.
A method to unite the security force pillars and disseminate targeting information is to advise and enable the local coordination center. The timeless adage states that information is power; so information sharing between all of the agencies in a central location multiplies the power of the entire security apparatus to be greater than each of the agencies individually. Advisors should harness this power by encouraging their partner leaders to utilize a coordination center for battle tracking, routine meetings, operational planning, and intelligence sharing. Advisors should also attend the events held at the coordination center as the prime venue to share releasable intelligence with their partners and synchronize their priorities to reflect those of the host nation. In Afghanistan, the coordination centers are known as the Operational Coordination Center (OCC) and they are arrayed at the tactical level at the provincial (P) and regional (R) levels. In one example in eastern Afghanistan, the OCC-P hosted two important meetings mentioned in the second tenet where ANSF pillars shared intelligence. During routine “Intelligence Shuras,” ANSF shared information on targeted individuals; at the “Security Shura,” the Provincial Governor established priorities for upcoming operations. The attending members from the National Directorate of Security (NDS), Afghan Border Police (ABP), Afghan Uniform Police (AUP), the Afghan National Army (ANA), and the Saranwal worked to nest their operations within a “collaborative security construct”[xxii] that sought to increase security through mutually supporting operations in depth[xxiii] along a restive border region. Together these agencies pooled intelligence that was utilized to issue warrants for targeted action within the F3EAD construct. Individually, each agency would have a tendency to process information within the stovepipe of their pillar, but the advisors continually reinforced the use of the coordination center for reporting and meetings to reduce the stovepipe. An example of the cross-pillar communication breakdown comes from law advisor Geoff Guska, a legal advisor in Iraq. “Efforts to obtain warrants were stove-piped within a particular staff section, which invariably failed to capture information, know-how, and host nation contacts possessed by other Rule of Law practitioners, that was required to work within the Iraqi criminal justice process. This fundamental misunderstanding of the criminal justice process coupled with the lack of contacts within the system led to many abortive efforts to obtain warrants.”[xxiv]
Overcoming the barriers to information sharing will prevent many pitfalls in the WBT process. Many security force agencies operating in a RoL environment may have a tendency to stay in their lane. Advising and influencing them to gather at an established meeting time and location like the OCC-P will create the synergy necessary for WBT.
7. Overlay the Overlay.
In order to assist host nation forces with warrant based targeting, the advisors and intelligence section must understand what assets are available to assist the HN with conducting EvBO. Many warrant-based targets originate from biometric data linked to improvised explosive devices (IED) or other nefarious activities. When the advisor force receives a new biometric match report, they must analyze the information using systems and databases such as Palantir,[xxv] Query Tree.[xxvi] The supporting unit’s intelligence section should use further forms of intelligence and different intelligence databases to search for the individual associated with the nefarious activity. Often, Coalition Forces have already detained biometric persons of interest once before because they were incidentally present at a previously targeted compound and may be targeted through further combined operations. Though CF routinely use biometric data in developing targets in Afghanistan, the host nation has developed a unilateral, Afghan sustainable method for warrant-based operations without the use of biometrics. Using the second and fifth tenets may gain the advisors and tactical unit limited visibility on this process and help the host nation find, fix, and finish the warranted individual.
In other cases, the analysis of national level intelligence collection provides persons of interest whom the advisors and unit can recommend their partners target. Once the intelligence section identifies a name and location, the advisor force should pass the releasable information to the host nation force in order to allow the force to initiate a warrant packet. During this time, the tactical force may also request Unmanned Aerial Vehicles (UAV) platforms to assist in developing the targeted individual and location. The intelligence section should strive to write this information in a manner releasable to the HN force as described in the eighth tenet. While the host nation force focuses on finding and fixing the enemy, advisors must ensure the CF intelligence section uses multiple intelligence disciplines to continue to develop and exploit warrant-based targets. The advisor force must utilize all intelligence systems, databases, and platforms available to overlay the overlays of information to maximize the intelligence input into warrant based targeting.
8. Classify Information at the lowest level.
When conducting WBT operations with host nation forces, the advisor force must ensure they complete proper training to display and release information to its partners. All U.S. personnel working with the HN should be familiar with the regulations of Foreign Disclosure and understand the difference between disclosure and release. Advisors disclose and release only the materials that are properly marked and reviewed by the unit’s Foreign Disclosure Officer (FDO) or Foreign Disclosure Representative (FDR) to the host nation force. The easiest way to release information to the host nation force is for the originating classification authority (OCA) to classify the material at the lowest classification level authorized. When the OCA classifies the information properly, the FDO is able to review the material and request the OCA to provide specific information to be display only or releasable to the host nation partners. Advisors must emphasize sharing information with their host nation partners in order to further the collaboration of information between the two forces and to continue to develop warrant-based targets.
To expedite the foreign disclosure process all tactical units advising host nation forces should have at least a FDR, if not an FDO. As soon as the intelligence section identifies an enemy of the host nation force, they must request releasable information from the OCA or through its foreign disclosure officer or representative. The unit’s FDO and FDR, in conjunction with the OCA, authorize advisors to disclose information required for WBT on a case-by-case basis. However, the FDO/FDR must ensure proper security of certain classified materials. For example, advisors should know that they may display certain information derived from sensitive systems to their HN partners. The FDO/FDR will not be able to disclose capabilities, equipment, and specific nomenclature. In addition, advisors should be aware that the process to release or display certain types of intelligence will be longer than others. After the FDO or FDR provides the releasable or displayable information, the advisor force should use its interpreters to translate the information, providing a comprehensive translated targeting card to their HN partners. Because conventional training methodologies do not include the FDO or FDR process, advisors must consider the timeline and process to disclose classified information when they mentor their host nation partners through warrant based targeting operations.
9. Hone a Specialized Strike Force.
There are many unique skills required for the ground forces that operate within the RoL. To best harness these skills, both the advisor force and host nation force should create a specialized strike force for partnered operations. This element must be suited for operations that both ‘find” targets and “finish” them in the F3EAD targeting model.
As discussed in the fifth tenet, many methods of developing warranted targets are exclusive to the advisor force. However, EvBO is sustainable by the host nation force and the specialized strike force should be knowledgeable of this process and proficient in its execution. This includes thorough tactical site exploitation (TSE), evidence handling, processing, and tactical questioning (TQ) to develop evidence utilized to both develop arrest warrants and exploit the case against targeted individuals. Within the RoL, physical evidence, sworn statements, testimonies, and the information derived from TQ by the host nation police officers offer the tangible evidence necessary for successful prosecution. The strike force must be skilled at finding the evidence, handling it properly, and successfully linking it to the targeted individual in court in order to add credibility to the security forces in the eyes of the judiciary and the local populace.
The specialized strike force will often find itself in the most hostile areas within the operational area. To both “find” targets through R&S patrols and “finish” them through cordon and searches and raids against dangerous insurgent forces, the specialized strike force must be well practiced in the implementation of proper security procedures. The strike force must be able to rapidly isolate a target compound or area in order to gain the tactical advantage over the persons of interest. Task organizing an isolation team within the strike force to accomplish this task is a must. Further, the isolation team should utilize the tactical call out (TCO) technique to gain entrance to a compound while not jeopardizing security and at the same time, not appearing heavy handed with the local populace.
The strike force must be proficient at integrating enabling teams to assist with EvBO. Several of these are Explosives Ordinance Disposal (EOD) to handle and remove explosive devices, Female Engagement Teams (FET) to search and question women where cultural sensitivities inhibit cross gender contact, and Tactical Explosive Detection Dogs (TEDD), which are trained to assist TSE and protect the strike force from booby trap threats. Further, the strike force must have highly trained medics who are organic within the element or attached to it. The medics not only provide skills to protect the strike force, but also may assist in the development of intelligence through interactions with the local populace.
The skills listed above require a specialized organization and pre-deployment training regimen for the strike force. Furthermore, the advisor’s strike force must be prepared to train their host nation partners in all of their TTPs. Partnered together, the strike forces are a valuable tool required to accomplish WBT within the RoL construct.
10. Advise the advisor.
The last tenet of implementing WBT encompasses the previous nine tenets and highlights the role of the advisor forces. The role of the security force advisor is crucial to moving the host nation systems forward. Advisor Geoff Guska observed in Iraq: “successful execution of warrant-based operations requires significant coordination with both the U.S. and host nation organizations.”[xxvii] Advising the advisor is the method to facilitate this coordination.

Figure 8: An Afghan Saranwal meets with the RoL advisor to discuss evidence and warrants at the OCC-P.
Highlighting the role of the advisor, the sixth tenet says that the host nation system must be sustainable and similarly the knowledge and skills imparted by the advisor force must persist long beyond the advisor. During home station training, many units participate in programs known as “train the trainer” courses to distribute knowledge from subject matter experts to the most junior Soldiers who need the skills. Similarly, combat advisors must advise the advisor to create subject matter experts in WBT who are able to share their knowledge of the process across their formation and across the other agencies with which they interact.
There are countless publications and training courses available to prepare security force advisors for their role that are outside the scope of this article, but it is important for the advisor to focus on creating a partner as equally skilled and knowledgeable in the RoL as themselves. Advisors may accomplish this by building the capacity of their counterparts and coupling this with many repetitions of WBT in order to gain the experience and confidence necessary to implement WBT within their unit. RoL should be a constant drumbeat when conducting key leader engagements with senior HN officials. As an internationally recognized measure of just governance, senior officials will appreciate this perspective from their advisors and seek to share it with their peers and subordinates. Other methods to advise the advisor are to create a cadre of specialized trainers who are able to train their own security forces with many of the special techniques and procedures required to conduct warrant based targeting as discussed in the fifth tenet. Several skills that will assist the F3EAD model for warranted targeting at the tactical level are TSE, TQ, evidence collection, and handling. Through repetition, the WBT skills of these key HN officials will improve and provide depth to the host nation’s ability to make WBT a sustainable system.
Derived from combat experience in Afghanistan as a model, this article provides ten tenets to assist combat leaders on advising host nation security forces to use WBT in the RoL. Warrants provide an extremely effective arrow in the quiver of a counter-insurgent force to improve security within their area of responsibility. Warrants simplify the detention process for the HN security forces by pre-approving targeted individuals for removal from the insurgency. Warrants provide legitimacy to the HN governmental officials as they provide tangible evidence to show family members, elders, and the local villagers to justify detentions on paper, verified with an official signature. The WBT process creates sustainable continuity by facilitating communication between the branches of the HN government and security forces, thereby increasing the synergistic energy of those forces. Understanding how to integrate the Army’s F3EAD targeting process in conjunction with WBT will provide an effective guide for the combat advisor to improve capacity of the HN security forces that they are charged to develop. Adopting the tenets of warrant based targeting presented here is one of the many adaptations derived from our recent OCO missions and a worthy tool for future military actions.
Bibliography
Gomez, J. A. (2011, July 16). The Targeting Process: D3A and F3EAD. Retrieved July 20, 2013, from Small Wars Journal: www.smallwarsjournal.com
Govern, K. H. (2012). Warrant-based Targeting: Prosecution-oriented capture and detention as legal and moral alternatives to targeted killing. Arizona Journal of International & Comparative Law, Vol. 29( No. 3), 484.
Government of the Islamic Republic of Afghanistan. (2004, 1 1). INTERIM CRIMINAL CODE FOR COURTS 2004. Retrieved from Rule of Law Afghanistan: http://www.rolafghanistan.esteri.it/NR/rdonlyres/0690C80A-4EB1-4AE1-907F-1DEB76D14A37/0/23CriminalProcedureCode.pdf
Guska, G. (2011, February 10). The Rule of Law at Dawn: A judge Advocate's Perspective on Rule of Law Operations in Operatoins Iraqi Freedom from 2008 to 2010. Retrieved from The Small Wars Journal: http://smallwarsjournal.com/jrnl/art/the-rule-of-law-at-dawn
Headquarters, Department of the Army. (26 November 2010). FM 3-60 The Targeting Process. Washington D.C.
ISAF Joint Command. (2012). FRAGO 230.01-2012 Amendement 01 to Support to Afghan-led Evidence-Based Operations. Kabul: ISAF Joint Command.
Kirkpatrick, S. (2013). TF 2-506IN Operational Key Tasks. Khost, Afghanistan: TF 2-506IN.
Palantir. (2013, October 17). Palantir Home. Retrieved from Palantir: https://www.palantir.com/
Query Tree. (2013, October 18). Query Tree. Retrieved from Query Tree: http://querytreeapp.com/
Work, P. (2013, April 25). "The find, the fix, and the finish". (J. Barta, Interviewer)
End Notes
[i] Interim Criminal Code for Courts (2004) [hereinafter ICCC]. (Government of the Islamic Republic of Afghanistan, 2004)
[ii] Ibid., Art. 30.
[iii] The reasons ANSF gave included: it was too dangerous to travel where certain targets lived, ANSF lacked the resources or personnel to make multiple arrests, the targets had fled out of the jurisdiction, and the targets were too elusive to catch. Although there is only anecdotal evidence to support the following assumption, the authors believe that the true obstacle was political. To arrest many warranted targets at once would incur political backlash from local leaders who straddled both the government and insurgent sides of the conflict in Afghanistan.
[iv] ICCC, Art. 21.
[v] Ibid., Art 34.
[vi] Ibid., Art 36.
[vii] Ibid.
[viii] ICCC, Art. 6.
[ix] See ICCC, Ch. 8 (laying out trial process and rights of the accused).
[x]ICCC, Art. 6.
[xi] Ibid.
[xii] FM 3-60 The Targeting Process (Headquarters, Department of the Army, 26 November 2010, pp. B-1).
[xiii] The Targeting Process: D3A and F3EAD, The Small Wars Journal (Gomez, 2011, p. 12).
[xiv] FM 3-60 The Targeting Process (Headquarters, Department of the Army, 26 November 2010, pp. 4-3).
[xv] FM 3-60 The Targeting Process (Headquarters, Department of the Army, 26 November 2010, pp. 2-1).
[xvi] “The Find, the Fix, and the Finish”: relief in place training lecture from 3rd BN, 187th Infantry (Work, 2013).
[xvii] Ibid.
[xviii] Warrant-based Targeting: Prosecution-oriented capture and detention as legal and moral alternatives to targeted killing, (Govern, 2012, p. 484).
[xix]The Targeting Process: D3A and F3EAD, The Small Wars Journal (Gomez, 2011, p. 14).
[xx] FRAGO 230.01-2012 – Amendment 01 to Support to Afghan-led Evidence-Based Operations (ISAF Joint Command, 2012).
[xxi] Ibid.
[xxii]TF Operational Priorities for 2nd BN, 506th Infantry (Kirkpatrick, 2013).
[xxiii] Ibid.
[xxiv] The Rule of Law at Dawn: A Judge Advocate's Perspective on Rule of Law Operations in Operation Iraqi Freedom from 2008 to 2010, Small Wars Journal (Guska, 2011).
[xxv] “Palantir builds software that connects data, technologies, humans and environments” (Palantir, 2013). An off the shelf commercial software program adapted for military intelligence work.
[xxvi] Query Tree is software that “uses drag and drop tools for exploring, analyzing and visualizing data” (Query Tree, 2013).
[xxvii] The Rule of Law at Dawn: A Judge Advocate's Perspective on Rule of Law Operations in Operation Iraqi Freedom from 2008 to 2010, Small Wars Journal (Guska, 2011).
